Exploring the Critical Components and Modern Solutions for Defending Computer Systems

In today’s digital ecosystem, the humble computer, whether a personal device, a workstation, or a point-of-sale system, forms the backbone of organizational productivity and data stewardship. Beneath their familiar interfaces, PCs are complex assemblies of interwoven systems, each with its own vulnerabilities. Understanding these layers and strategically fortifying them is crucial for any modern enterprise.
Unpacking the Layers: What Makes Up the PC?
A computer is far more than its physical shell. At its core, it comprises several critical layers, each serving distinct roles and presenting unique security challenges:
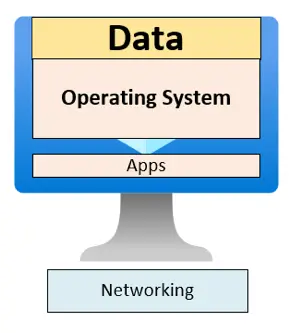
- Data: The crown jewel of any system. Every mechanism—hardware, software, or policy—is ultimately deployed to safeguard the information that drives business operations.
- Operating System (OS): The engine of interaction, the OS enables users to manage files, run applications, and communicate across networks.
- Applications: Third-party software layered atop the OS, from office suites to custom business apps, facilitate productivity and data interaction. However, these often introduce additional avenues of risk.
- Networking Layer: Connectivity transforms isolated computers into components of a broader ecosystem, opening doors for collaboration as well as external threats.
Vulnerabilities: Where Do Threats Lurk?
While each layer is indispensable, they also create distinct vectors for exploitation:
- Operating System Weaknesses: Recognizing the OS as the system’s central nervous system, vendors routinely issue patches to remediate new-found vulnerabilities. Timely patch management is critical; delays can leave exploitable gaps.
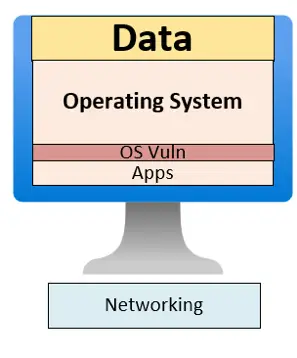
- Application Vulnerabilities: Unlike OS updates, application patching is inconsistent. Some apps never receive updates, and many organizations lack visibility or processes to remediate these weaknesses. This creates a persistent attack surface—cybercriminals often chain application and OS exploits to achieve compromise. Only remediating the OS and not the applications makes it so that there is always an attack vector waiting to be exploited under the right circumstances.
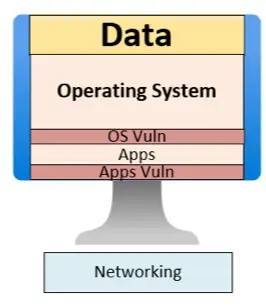
The interplay of these vulnerabilities is particularly insidious. Remediating one while neglecting the other merely shifts the risk rather than eliminating it. A neglected app, paired with an unpatched OS, can spell disaster. That’s why a holistic, layered defense is vital.
Proactive Defense: Modern Recommendations for Robust PC Security
True cyber resilience transcends reactive measures. By adopting a multi-pronged approach, organizations can move from vulnerability to vigilance:
Firewall SOC: Active Oversight at the Perimeter
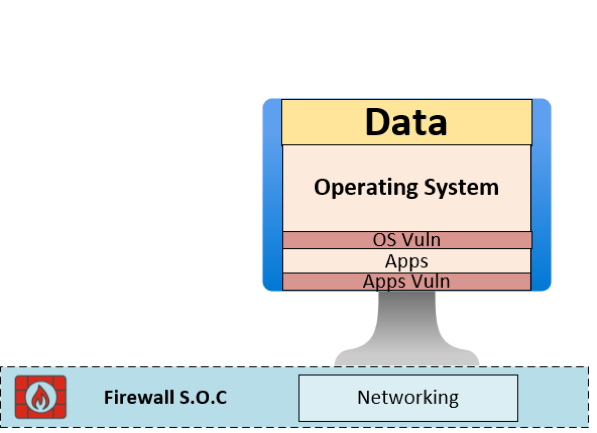
Deploying a firewall is foundational, but it’s just the beginning. Integrating firewall monitoring with a Security Operations Center (SOC) elevates defenses by:
- Ensuring real-time scrutiny of all inbound and outbound traffic
- Rapidly flagging anomalies and potential breaches
- Holding the firewall accountable—no more “set and forget”
Round-the-clock oversight ensures any unusual event is investigated immediately, reducing response times and containing threats before they escalate. To learn more about our Security Operations Center and how we use firewalls, check out our SOC article here.
Software Asset Management & Vulnerability Scanning: Visibility is Key
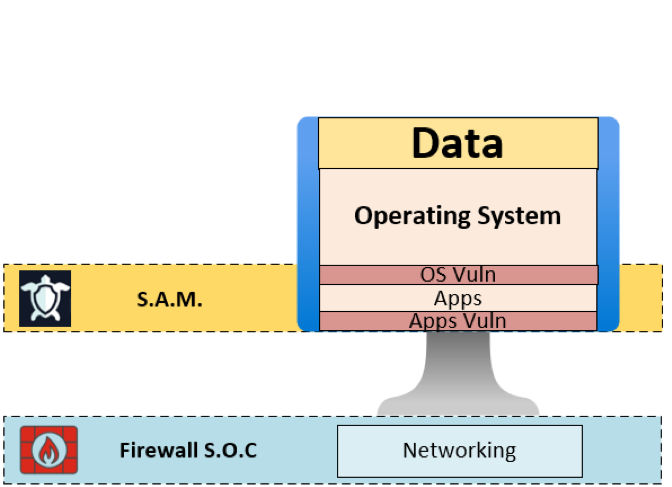
The sheer diversity of applications running on modern PCs makes comprehensive oversight challenging. Employing a rigorous software asset management program, coupled with automated vulnerability scanning, allows organizations to:
- Catalog all installed applications across endpoints
- Identify unpatched or unsupported software
- Prioritize remediation efforts based on severity and business risk
Proactive scanning closes the window of opportunity for attackers, shrinking the available attack surface across the enterprise. If you’d like to know more about our S.A.M. options, check out our Case Study on Vulnerability Scanning.
MDR SOC: Managed Detection & Response for Advanced Threats
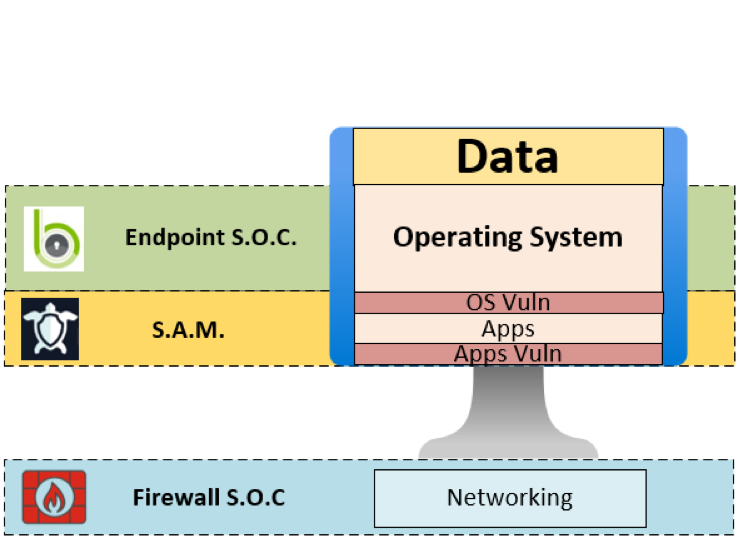
Beyond firewalls and asset management, Managed Detection and Response (MDR) provides a safety net. By combining automated threat intelligence with expert human analysis, MDR SOC teams can:
- Detect sophisticated, multi-stage attacks—many of which bypass traditional defenses
- Respond quickly with tailored containment and remediation strategies
- Continuously improving security posture through ongoing threat hunting
This blend of technology and expertise delivers a robust, adaptive defense—essential for today’s unpredictable threat landscape. To learn more about how we use the SOC to secure endpoints, click here.
Data Loss Prevention: Protecting the Crown Jewels

Ultimately, all security controls converge toward a single goal: safeguarding sensitive data. Data Loss Prevention (DLP) solutions monitor data in transit, at rest, and in use, alerting teams to suspicious activity and enforcing policy controls. By layering DLP atop OS, application, and network defenses, organizations can:
- Prevent unauthorized data exfiltration, whether accidental or malicious
- Ensure compliance with regulatory requirements
- Maintain customer trust and operational continuity
If you’re interested in understanding more about DLP and how we view it at H&D, check out our Project: Case Study here.
Conclusion: The Case for Layered, Proactive Security
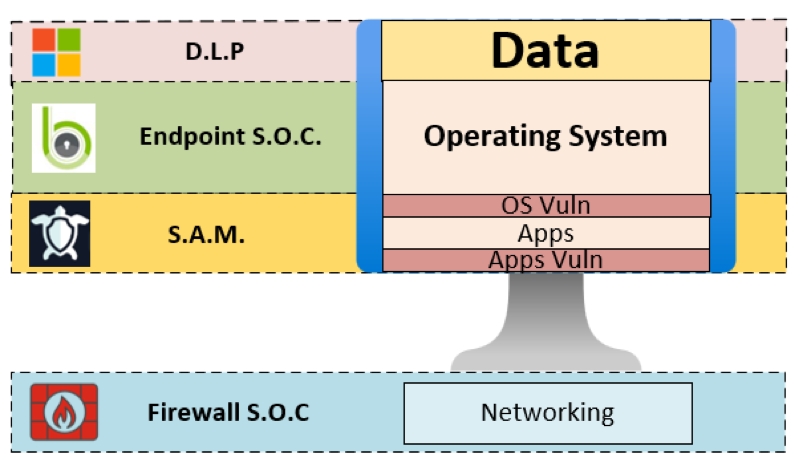
Modern PC security is a journey, not a destination. Each layer—data, OS, applications, and network—presents both a target and an opportunity for defense. By embracing continuous monitoring, intelligent patch management, and layered protection strategies, organizations transform their approach from isolated fixes to true cyber resilience.
In today’s hyper-connected world, settling for anything less than proactive, multi-layered security is no longer an option. Through vigilant oversight and comprehensive controls, businesses can meet threats head-on—defending not just their systems, but their mission and future.









